Intro
This blog by Damien Destrez goes over an incredibly interesting use case for MAC Policy within Aras Innovator. If you're unfamiliar with MAC Policies we have an introduction blog which can be found here, as well as another concrete example here.
If you prefer to watch the video tutorial, you can find it here.
Mandatory Access Control principles
- First, a MAC Policy is a feature that by default is not activated on any ItemType, it's available to introduce specific business requirements around Security.
- When active, MAC policies are a MANDATORY LAYER that cannot be skipped or bypassed.*The rule can include some specified Exempted User and/or Group of User
- MAC policy basically compare properties from the logged in User and an Item:
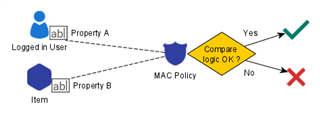
Businesses that can be supported by MAC Policy
- Company secrecy: https://en.wikipedia.org/wiki/Secrecy
- Handling Confidential Documents
- National classification: https://en.wikipedia.org/wiki/Classified_information
- National security documents, Items, classified pieces of information
- Export Control / Licenses:https://en.wikipedia.org/wiki/Export_control
- Military equipment following rules like ITAR, EAR, EU, NATO, etc.
- Corporate policy protecting IP during a specific phase
- Hide data created by some critical R&D departments
Data Model changes required
As MAC Policy is comparing properties between a User and an Item, we need to add to both ItemTypes for the properties that will be compared.
We will use as an example the Secrecy Level on Documents.
The end result that we need to prove is that a User with a Secrecy Level lower than the one set on the Document cannot access the Document.
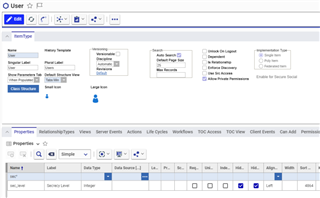
New property on User
Add a new Property:
- Name = sec_level
- Label = Secrecy Level
- Data type = Integer
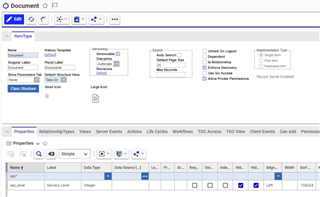
New property on Document
Add a new Property:
- Name = sec_level
- Label = Secrecy Level
- Data type = Integer
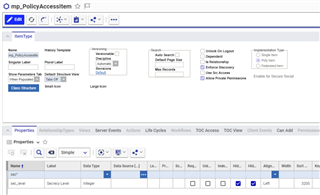
We need to modify the ItemType: mp_PolicyAccessItem by adding the EXACT same property as the one just added on the ItemType: Document.
Add a new Property:
- Name = sec_level
- Label = Secrecy Level
- Data type = Integer
Create a MAC Policy
As an Administrators, go into the TOC -> Administration -> Access Control
And then click "MAC Policies" / Create new
- 1. Enter a Name (can have some space), and a Description if needed
- 2. Into the TAB "Applied To", add the ItemTypes you want to activate this MAC Policy (in our case, Document)
- 3. Into TAB "Exempt Identities" we can add Identities (User / Group of Users) that would skip this rule
- 4. Save
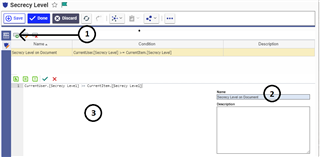
Then we go into the Policy Rule Editor
- 1. Click into the bar on the "New Condition" icon (first from the left)
- 2. Set a Name on the bottom right
- 3. Create the Rule by directly starting to type on the bottom left
- CurrentUser.[Secrecy Level] >= CurrentItem.[Secrecy Level]
- 4. Save the MAC Policy
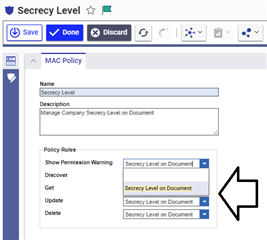
Then you need to set Rule policy
- 1. Go Back into the main Form
- 2. Into the section "Policy Rules" set your rule on all "Accesses"
- 3. Save the MAC Policy
Activate a MAC Policy
Once you have saved your MAC Policy and its rules
- 1. Go into the Action menu
- 2. Click on "Activate"
- 3. A message will tell you when the MAC Policy is active

Modify a MAC Policy
If you need to modify an Active MAC Policy
- Into the Action Menu, first click on Deactivate
- Then in the same menu, click on "New Version"
- Then you can modify your MAC Policy as you wish
- Save your changes
- And finally, into the same menu, click on "Activate"
Daily Usage
Once you have everything setup, you need to modify your Forms (User + Document) to set the values.
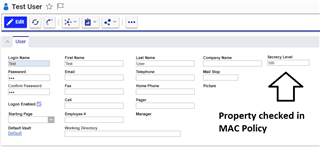
And when a User will need to create a Document or modify one, the Secrecy Level will appear.
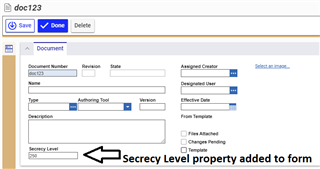
Here you can add any Business logic on the Client / Server side in order to avoid people creating documents on a Level that is above their own, or any other business logic.
The result will be, any Document created with a Secrecy Level superior to the User's one, won't be accessible by the user.
How to test
Log as an Administrator (i.e. admin)
- Create multiple users with different Secrecy Level
- Create 2 documents with the following Secrecy Level values.
|
Document Secrecy Level |
||
|
200 |
600 |
|
|
User 100 |
BLOCKED |
BLOCKED |
|
User 500 |
Accessible |
BLOCKED |
|
Admin |
Accessible |
Accessible |
Once those 2 Users and 2 Documents are created you can test that as follow:
- Connect as User100
- When running a Search for Document, nothing appears
- Connect as User500
- When running a Search for Document, only the 200 documents should appear
- Connect as an Administrator (.i.e. admin)
- When running a Search for Document, both documents should appear

